Joint Cybersecurity Advisory Fails To Capture Non-Technical Aspects Of Attacks
A joint cybersecurity advisory has been issued by the Australian Government alongside the US, UK, and FBI. The report highlights the top 30 vulnerabilities currently exploited by cyber criminals. Officials warn that delays in patching these flaws leave systems exposed to attacks.
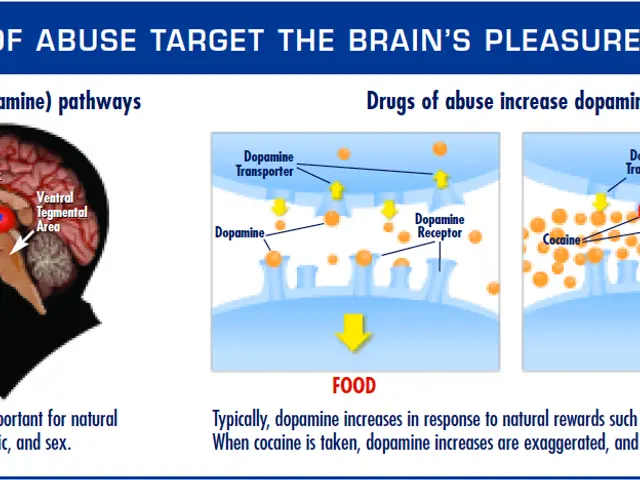
The advisory lists critical weaknesses in software from Microsoft, Pulse, Accellion, VMware, and Fortinet. These platforms are now prime targets for malicious actors. Four of the most exploited vulnerabilities in 2020 involved remote work tools, VPNs, and cloud-based systems.
Paul Chichester, a cybersecurity expert, noted that the shift to remote work has made patch management harder. Many perimeter devices remain unprotected due to inconsistent updates. The Australian Cyber Security Centre (ACSC) is urging organisations to adopt centralised patch management to close these gaps. While patches are available for all 30 listed vulnerabilities, the advisory does not address human error as a contributing factor. Jacqueline Jayne, a Security Awareness Advocate at KnowBe4, stressed the need for better training alongside technical fixes. She argued that education must play a key role in reducing risks.
The Australian Government and its partners continue to push for stronger cyber defences. Patches for all listed vulnerabilities exist, but organisations must apply them promptly. Without proper updates and training, systems will remain at risk of exploitation.